Curve Dao Token (CRV) has been in decline since Sunday after Vyper developers detected a series of hacks. Vyper announced on Twitter on July 30th that versions 0.215, 0.2.16, and 0.3.0 were vulnerable to faulty reentry locks. The announcement also stated that the incident was being investigated and projects based on these versions should be contacted immediately.
Curve Finance promptly acknowledged the attack and tweeted the following:
“A series of stable pools (alETH/msETH/pETH) using Vyper 0.2.15 have been exploited due to a faulty reentry lock. We are assessing the situation and will update the community as things develop. Other pools are safe.”
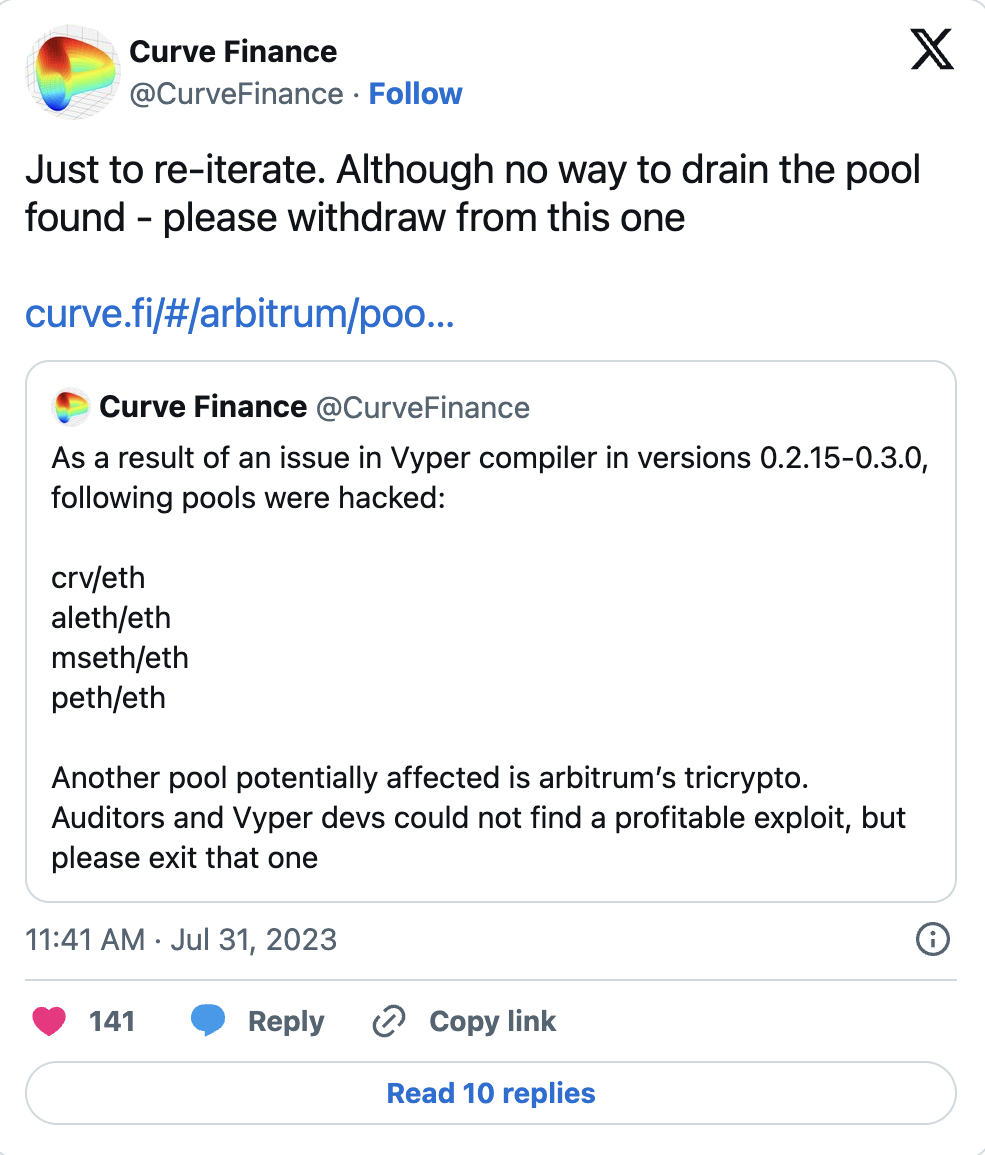
Affected Pools in Curve Hack
Curve Finance initially stated that three pools were affected by the Curve hack, but the decentralized finance (DeFi) platform later acknowledged that the crv/ETH pool was also affected, bringing the total number of affected pools to four.
While Curve Finance claimed that the hacker(s) couldn’t access the funds in the compromised pools, the platform urged its users to withdraw their funds from these pools as a precautionary measure against the possibility of the hacker bypassing the auditors and Vyper developers.
How Did the Hack Happen?
Most people, including developers, agree that the Curve Finance hack wouldn’t be something a typical researcher would look for. The hacker thoroughly examined the protocol’s version history to find a flaw that could be exploited and put millions of people at risk. The hacker spent a significant amount of time identifying the security vulnerability.
Curve Finance emphasized that the best way to avoid chaos was to transition to contracts using the latest versions. In a tweet, Curve Finance announced that the Vyper 0.03.7+ version had been thoroughly audited and revamped. The announcement also stated that while this was not a foolproof method, transitioning to contracts using the latest versions would be preferable.