It is not a day without a new security vulnerability causing cryptocurrency investors to lose millions of dollars. Today, many smart contracts have been attacked. The price of a popular altcoin trading on the Binance exchange has significantly dropped. So, how did the attack happen? What will happen now?
Cryptocurrencies with Hot Developments
Seven smart contracts coded with certain versions of Vyper were hacked today. A total loss of 28 million dollars was experienced. The pools on Curve Finance were attacked. The critical security vulnerability is known as reentrancy. This is a critical security vulnerability that occurs when an external call (external request) to a contract is interrupted and recalled before completion, which can potentially be exploited by attackers.
This security vulnerability led to a significant amount of money, over 26 million dollars, being withdrawn from various related pools. According to security analysts at Beosin, the attackers targeted pools consisting of multiple projects from Curve.
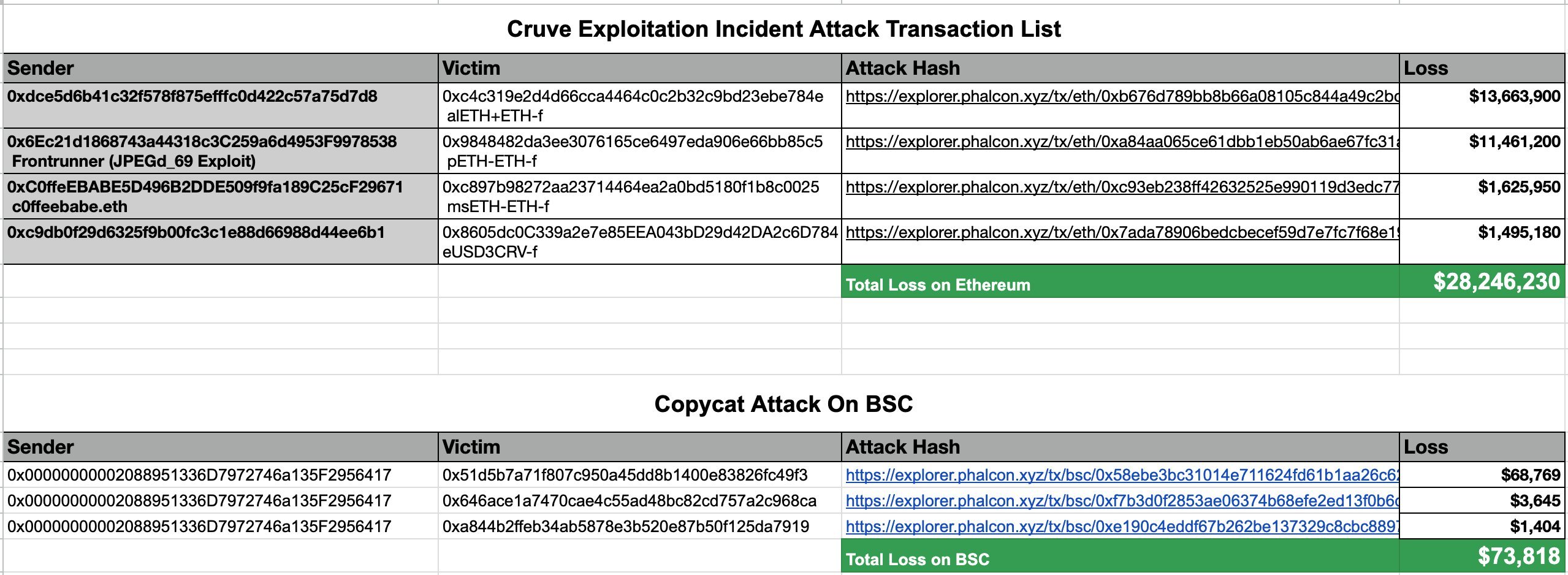
JPEGd saw an 11.4 million dollar withdrawal from the ETH-ETH pool on Curve. Following closely, there was a movement of 1.6 million dollars in the sETH-ETH pool of Metronome. However, the alETH-ETH pool of Alchemix witnessed the most significant activity with a transaction worth 13.6 million dollars.
Cryptocurrency Hack
As explained by Igor Igamberdiev, the research director at Wintermute, this was associated with certain older compiler versions of Vyper, the programming language used to write the code for these pools. The attackers who identified smart contracts coded with the older version managed to empty these pools using flash loans.
It was announced that versions 0.2.15, 0.2.16, and 0.3.0 of Vyper were vulnerable to faulty reentrancy locks, and investigations are ongoing. Initial reactions emerged with concerns over a major security breach, while on-chain data indicates that MEV bots may have executed some of these transactions in advance. This situation has led to speculation that white hat hackers may also be involved.
According to Banteg, a participant in Curve, the CRV pool was emptied minutes before the white hat operation for system security.