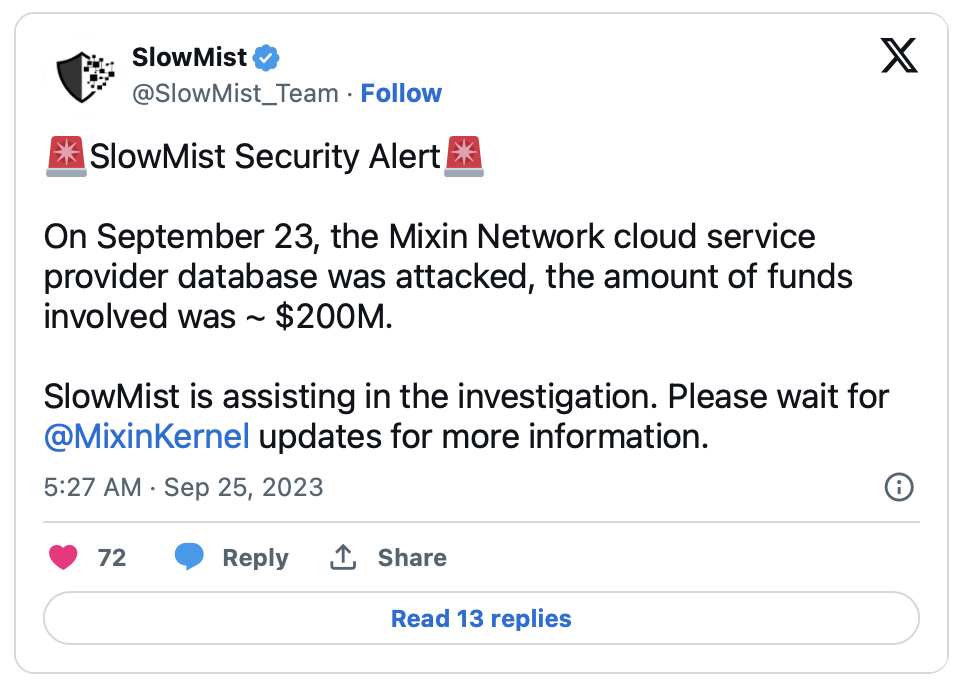
Mixin Network, originally positioned as a decentralized exchange (DEX) and endorsed by the renowned Chinese influencer Li Xiaolai, has been targeted by a major hack on September 23rd, resulting in the theft of over $200 million in crypto assets.
Deposits and Withdrawals Suspended
SlowMist, a blockchain security firm, reported that Mixin Network, a decentralized exchange supporting 48 public blockchains and with a total asset value exceeding $1 billion, has fallen victim to a massive hack resulting in the theft of over $200 million in crypto assets.
In the aftermath of the incident, Mixin Network has temporarily suspended its deposit and withdrawal services. Following extensive discussions and unanimous consensus among all network nodes, it is expected that all suspended services, including deposit and withdrawal operations, will be resumed once the identified security vulnerabilities are confirmed and rectified.
While the suspension does not affect fund transfers, the Mixin Network team will share details on how they will handle the stolen funds in the coming hours.
Special Announcement Regarding the Stolen Funds
The Mixin Network team stated that they will provide a detailed solution for the stolen funds at a later time. In a statement, the founder of Mixin Network, Feng Xiaodong, announced that he will address the concerns in a live Mandarin broadcast on September 25th, 2023, at 13:00 Hong Kong time (08:00 GMT). The announcement will be summarized in English for better understanding. We will do our best to minimize the losses and sincerely apologize for the incident.
Crypto scams and attacks are rapidly increasing despite various security measures. Just last week, Fortress Trust experienced a $15 million crypto theft, where the attacker took control of Retool’s Google Authenticator cloud synchronization feature. Retool announced that the hack affected approximately 27 cloud customers.
The hack attack was initiated through an SMS phishing strategy targeting Retool’s personnel. The hackers cleverly impersonated members of the IT team and directed recipients to click on a supposedly legitimate link discussing a fictitious payroll topic. Unfortunately, one employee fell victim to this phishing scheme and disclosed their login credentials to the trap.