Although blockchain technology offers extraordinary market conditions to its users, the biggest problem in the ecosystem is the inadequacy of security measures. In this regard, a method developed by hackers has made a significant impact. This method, used on BNB Smart Chain (BSC), shows a new way for hackers to manipulate smart contracts and distribute malicious software to take over users’ assets.
New Threat Detected on BSC
This technique, introduced as EtherHidding, was reported and shared by researchers at Guardio Labs, a blockchain security company, on October 15. It revealed that this type of attack involves injecting code that takes partial code series from blockchain contracts and puts WordPress websites at risk. Attackers hide code data in BSC smart contracts, presenting them as an anonymous free cloud service system.
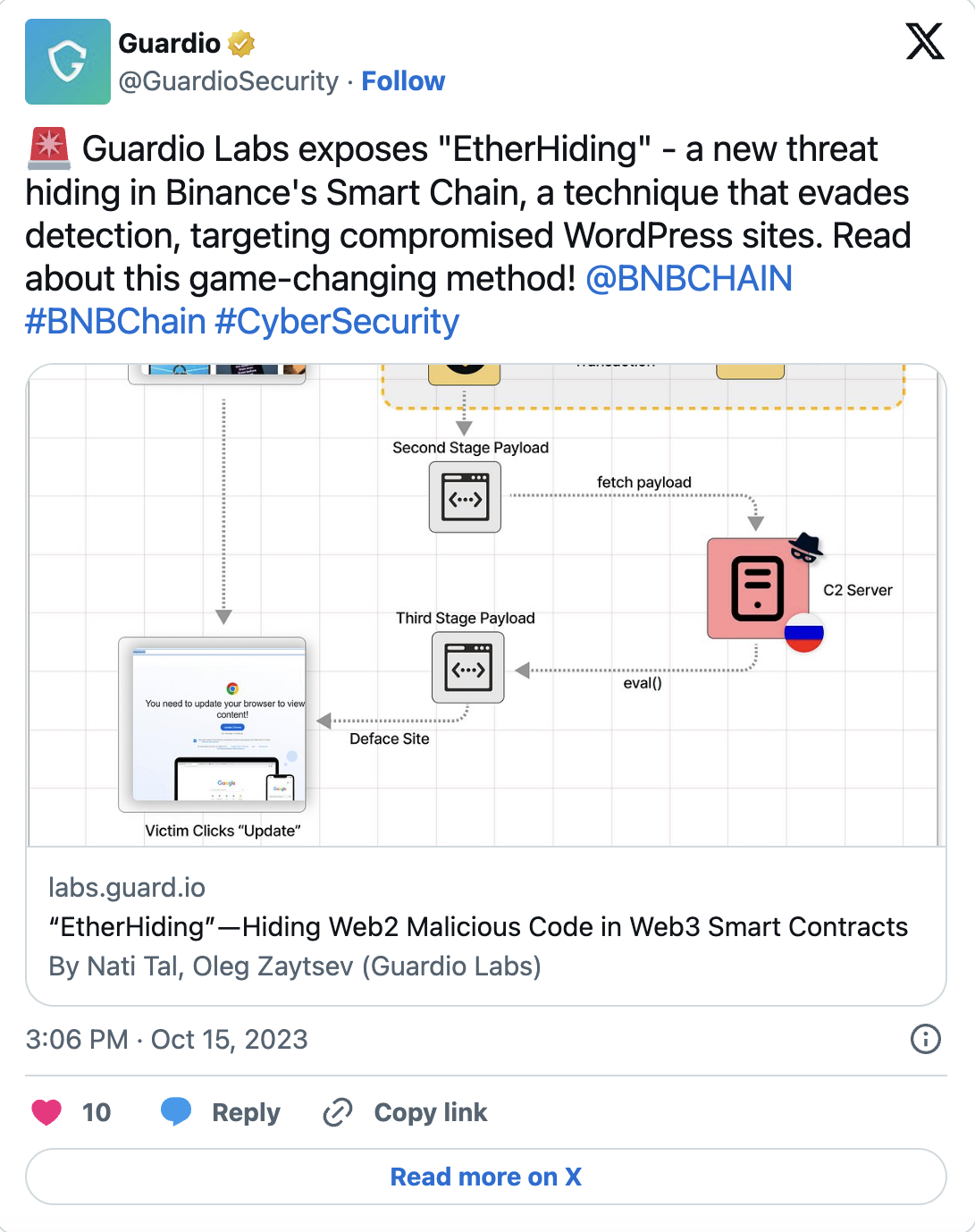
Hackers can update these codes and change their attack methods whenever they want. Recent attacks have involved directing victims to a fake landing page, requesting them to update their browsers as a fake browser update.
The code series contains JavaScript that brings additional code from the attacker’s domains. This method ultimately leads to serious victimization with fake browser update notifications containing malicious software.
What Can Users Do?
This hacking method allows victims to easily change the malicious code and alter the attack chain with each new blockchain transaction. According to Nati Tal, the Head of Cybersecurity at Guardio Labs, and Oleg Zaytsev, a security researcher at Guardio Labs, this makes it difficult to counter the attack.
Once the smart contracts infected with the virus are deployed, they operate according to the attacker’s requests. Binance‘s only option in this regard is to rely on the developer community to flag malicious code in the contracts after they are discovered.

Guardio Labs emphasized that website owners using WordPress, which powers approximately 43% of all websites, should be extra vigilant about their security practices before performing updates:
“WordPress sites are highly vulnerable and frequently targeted, as they serve as primary gateways for these threats to reach a wide pool of victims.”