Once, aggressive hackers found banks to be the most lucrative targets for cyberattacks. However, these have remained challenging targets. Last year, we discussed the legendary bank hack case of Lazarus, where various attacks like social engineering and system breaches led only to millions of dollars in booty. However, things are much simpler in crypto.
Millions Dollar Hack
On June 20, Slingshot’s official Twitter account was hacked, and users were directed to a bogus token address. So far, at least 216 user addresses have been stolen. According to experts, the attacker was none other than the infamous cybercrime group Pink-Drainer, who has previously used the same method to attack several well-known web3 project’s social platform accounts.
The attackers who seized Slingshot‘s address were extremely professional. The hackers created an exact replica of the decentralized exchange and directed victims to this fake site through a different domain. The domain extension was the only difference, and even regular platform users couldn’t be certain whether it was fake or not. Many projects and internet sites with the same name have different domain extensions, which are usually redirected to the main domain.
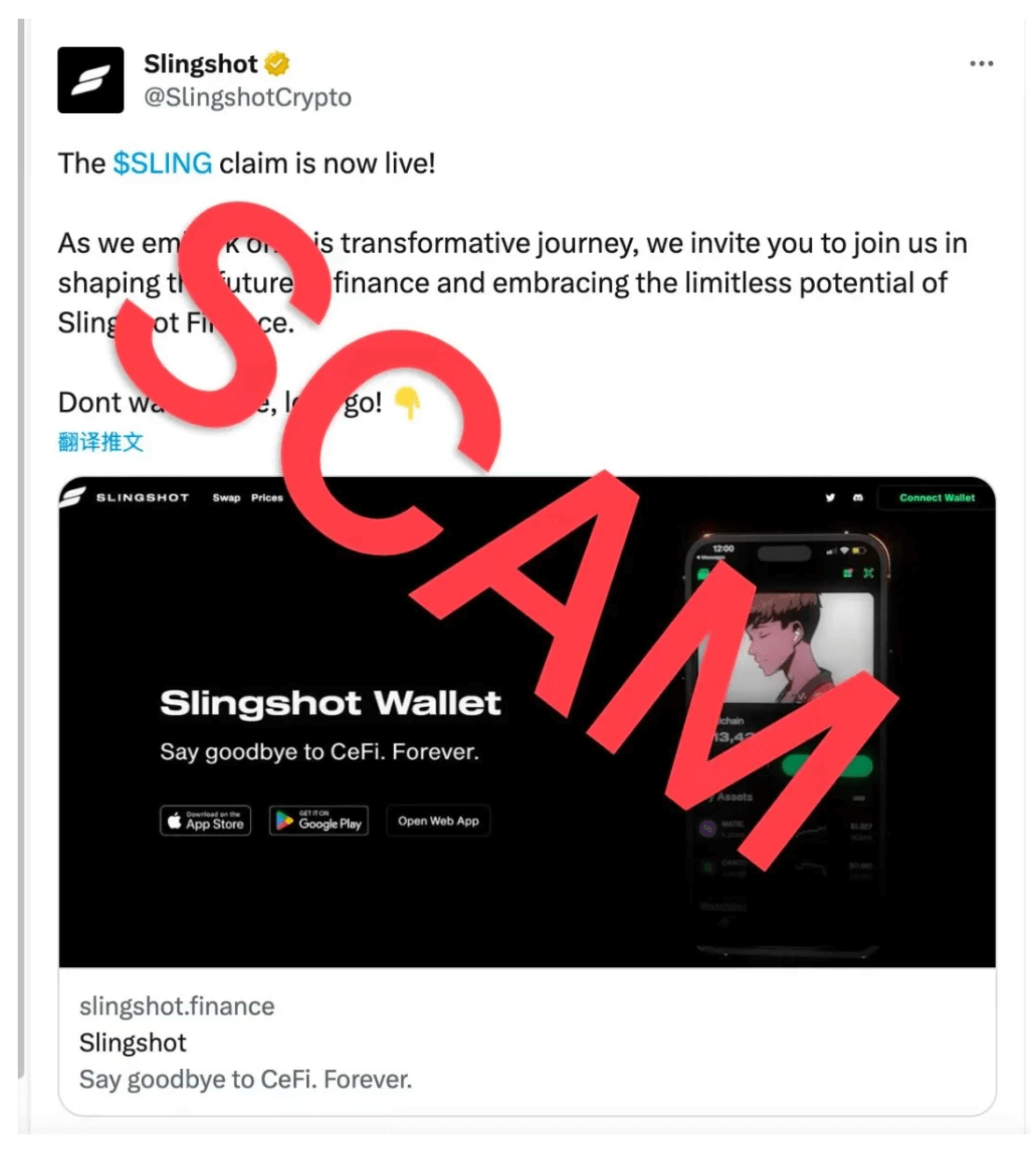
They made the above post and redirected investors here. The attack was disguised as a marketing ploy for the platform’s so-called token “SLING.” Those who connected their wallets to the fake internet site also granted the hackers management permissions for their wallets. They then pocketed over 3 million dollars in booty.
The Pink Drainer hacker group had also taken over many popular accounts like OpenAI CTO, Orbiter Finance, Evomos, Pika Protocol, and emptied investors’ wallets using similar methods.
Crypto Hackers’ Motivation
Today, hacking centralized crypto exchanges is similar to hacking banks in the past. The attackers move the money in small parts and accept the possibility of being detected. Moreover, security was top-notch. However, the situation is much different in crypto protocol or decentralized wallet hacks. With just a few clicks, those who can deceive the victim become the authority over the wallet. They can transfer the victim’s balance to themselves forever (as new balances are added) with their smart contracts.
Remember that if you use a decentralized wallet, the risk of “hackers” getting caught is lower, and they can hack you more easily. Be aware of this while continuing to use your wallet as an extension in the browser or as a mobile application. However, while doing this, you should be careful about what you “click” on. Especially during signing transactions, you should think 40 times, check the address, the contract address, etc., and then click the mouse. Or there’s an easy way: install your decentralized wallet on a secure computer that you don’t actively use and only use it when your mind is clear (the risk of being deceived is low). You can perform the transactions you want to take risks (testnet, etc.) on another computer that you actively use, with another wallet.