For cyber attackers, cryptocurrency investors are among the most lucrative targets, and they work intensively. In the past, ransomware and cyber attacks on banks were notorious. However, times have changed, and with crypto, they can easily access a lot of loot. So why does their latest targeted method concern everyone?
Cryptocurrency Theft Method
Social engineering-supported attacks allow hackers to empty people’s wallets with mind-boggling stories. The more sophisticated the story, the higher the attackers’ chances of success. We saw Lazarus approach some team members with job offers to obtain protocol keys during the Ronin bridge hack. They stole over $600 million in cryptocurrency.
Now, they set pinpoint traps for smaller targets. This directly targets people who are popular on social media or known to have significant investments, forcing them to be more cautious.
Real-Life Attack Example
One of the most famous on-chain detectives in crypto, ZachXBT, is also a very good OSINT expert. He has made a name for himself with the cases he has solved and shared the details of an interesting case he received about an hour ago.
“Here is an overview of one of the best-executed scams I’ve seen recently, which I wanted to share with the community as a cautionary tale. A few weeks ago, I received a DM from a follower who lost $245,000 after accidentally downloading malware onto his computer.”
“The incident began when an account claiming to be Peter Lauten from a16z messaged a team for information about a potential podcast partnership.”
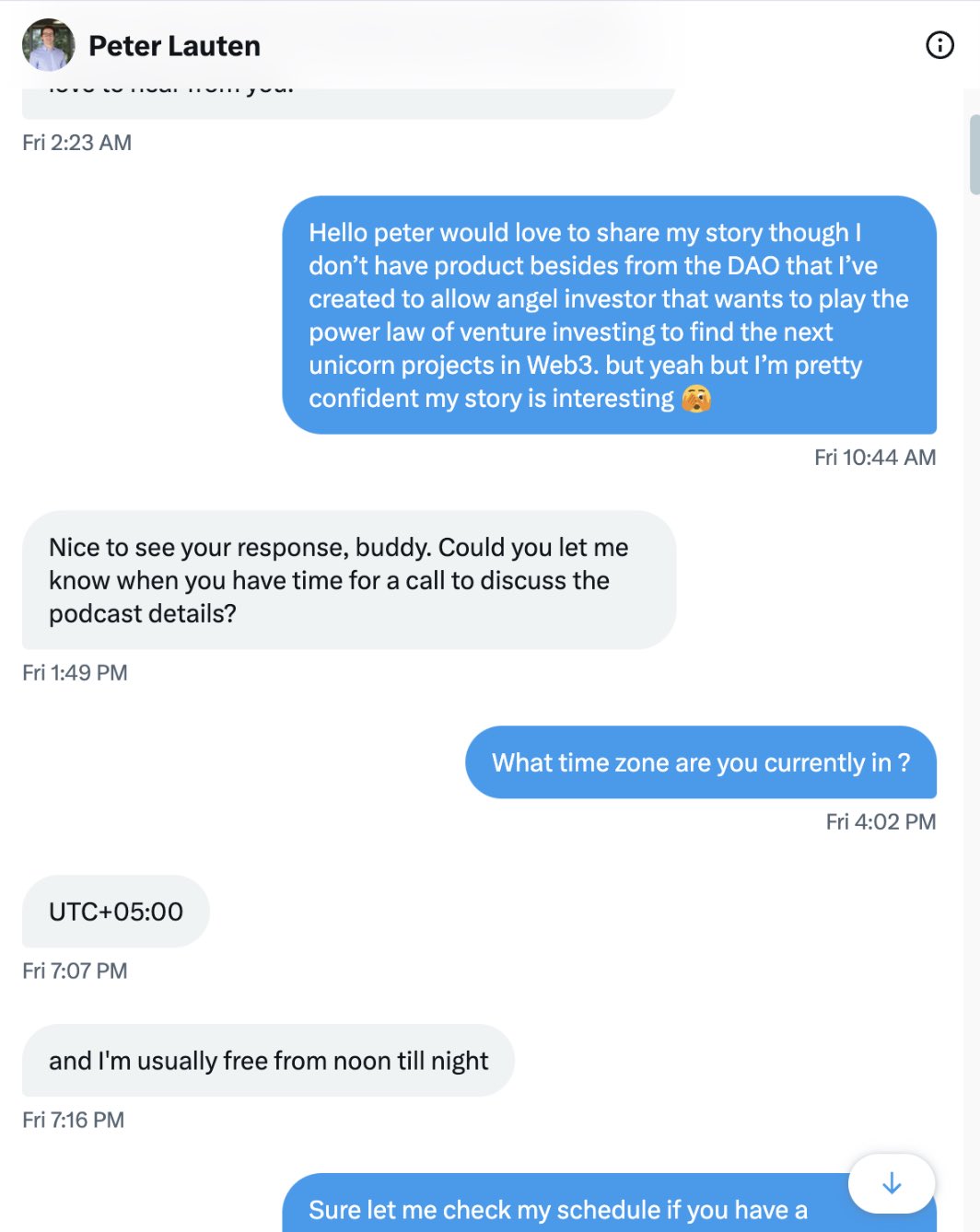
“The attacker noticed that the real Peter Lauten had changed his X (Twitter) username to ‘peter_lauten’.
He changed it to ‘lauten’ and then reclaimed his old username.”
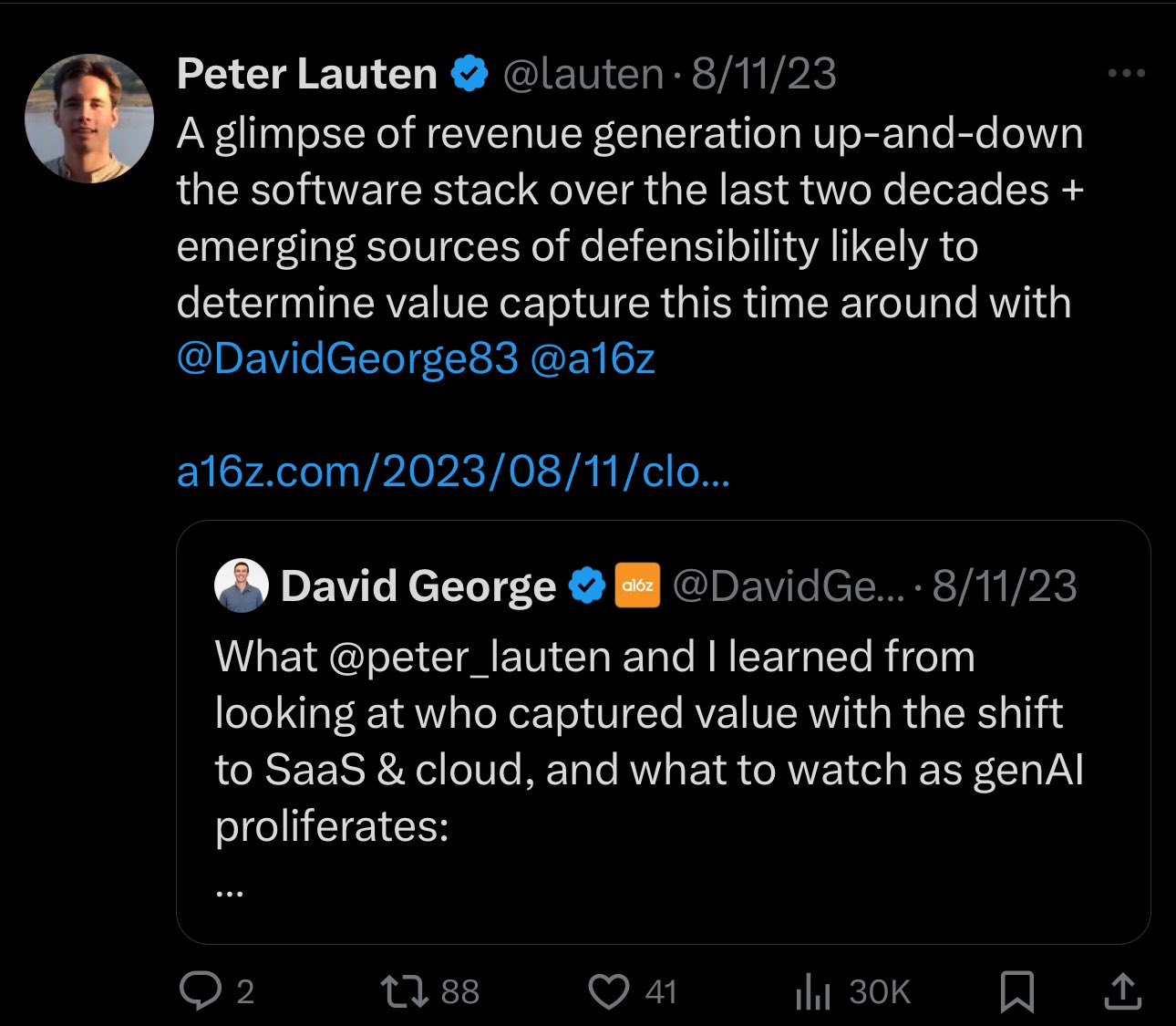
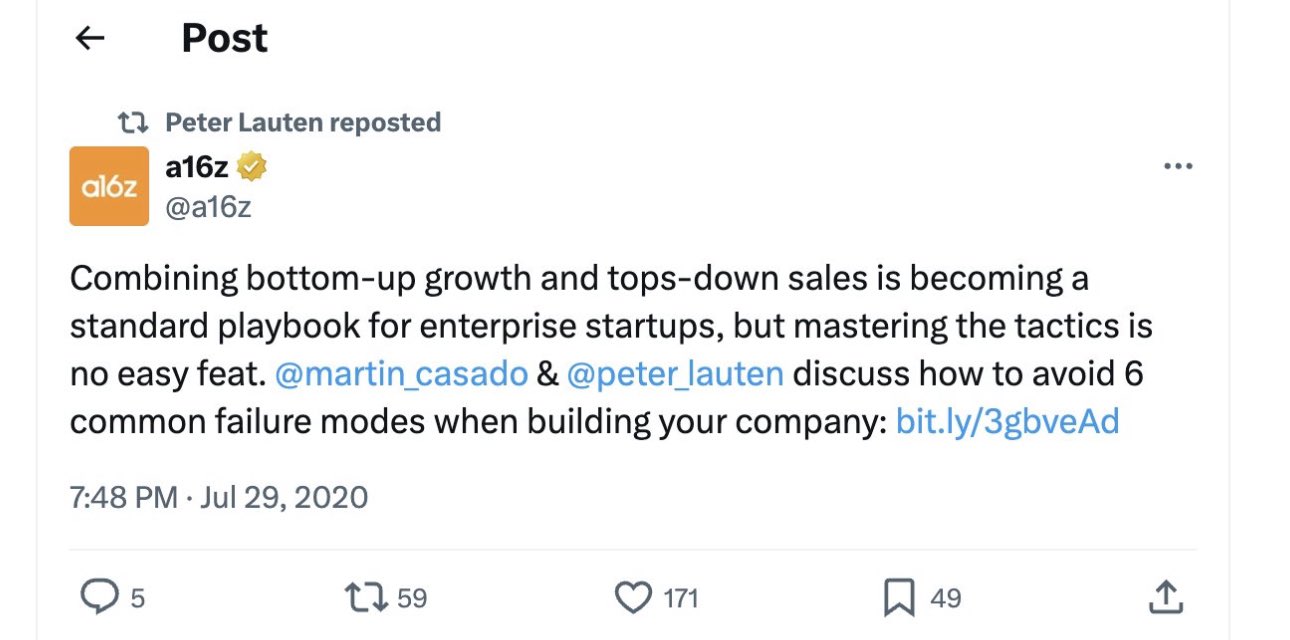
“However, the problem was that the a16z website was still linked to the old username, and a few posts from the a16z X account tagged the old username.”
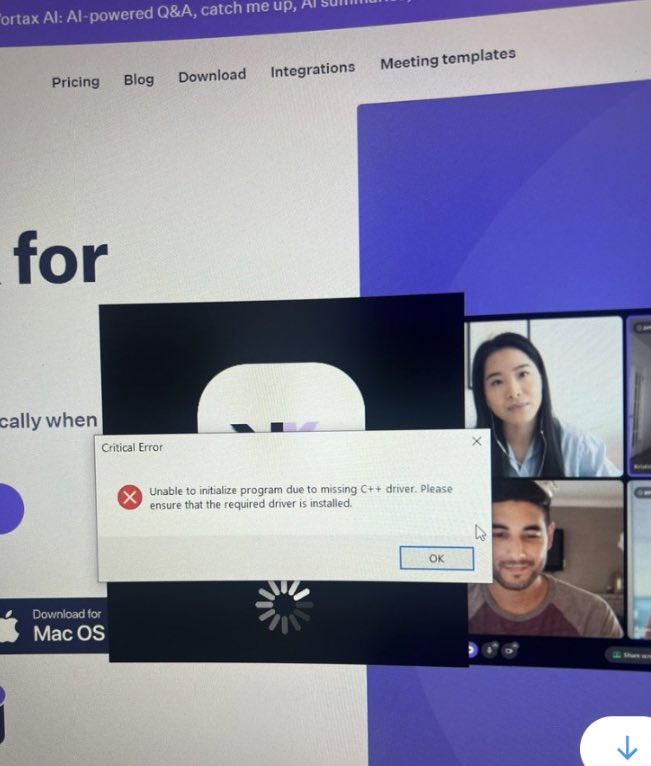
“Unaware of this, the victim was later socially engineered by the impersonator to install a fake meeting application called ‘Vortax’, which was actually malware, on his device. Shortly after the download, the victim’s crypto assets were transferred from their wallets.
The funds were then moved through multiple intermediary addresses and deposited into exchanges.”
Preventive Measures
The victim paid the price for carelessness and excessive skepticism by losing $245,000.
The famous crypto detective offers a few tips on this matter;
- If you change your username, inform the company you work for
- Never download random files (this is always very dangerous)
- Check the mutual follower ratio (useful unless an account is compromised)
- When searching for Vortax on X, there are warnings about the site. Thoroughly research any application you plan to download
You can use virtual servers for risky applications. Otherwise, a virus entering a useless application connected to the same internet could cause data leaks from your other devices. Even updated anti-virus programs may not recognize encrypted malware for some time. Unless someone is constantly monitoring the packets your device sends out to ensure your security, it is advisable not to install anything on your device other than well-known applications (from official websites).

 Türkçe
Türkçe Español
Español