An attacker allegedly tricked a user into sending them Wrapped Bitcoin (WBTC) worth $68 million and later sent back $153,000 in Ethereum as a supposed gesture of goodwill. In the same transaction, the attacker sent a message agreeing to negotiate and requested a Telegram username from the victim to establish contact. The amount returned represents only 0.225% of the total funds claimed to be stolen.
Noteworthy Move by the Attacker
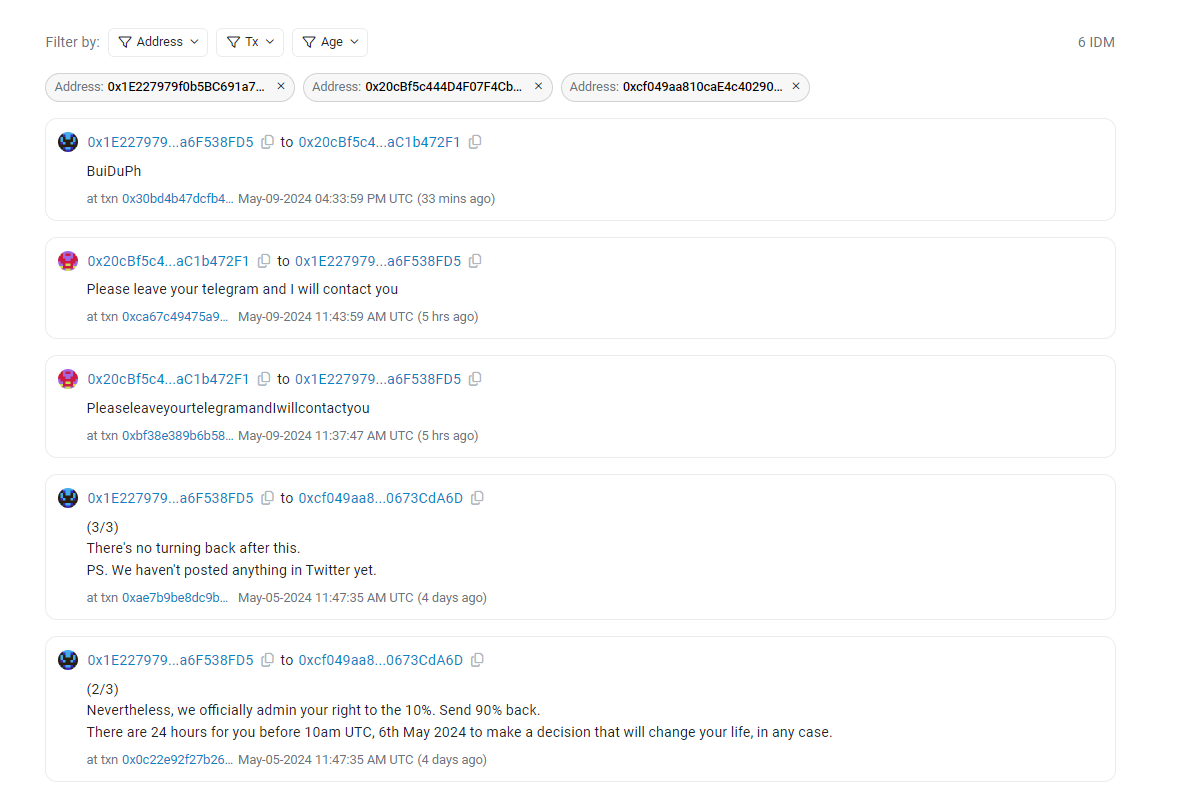
Blockchain data from May 5 shows the victim’s account, ending in 8fD5, sent three messages to an account ending in dA6D. The recipient had received funds through several intermediary accounts from the FakePhishing327990 labeled attack account, suggesting that dA6D was likely controlled by the attacker.
The messages implied that the victim was willing to give the attacker 10% of the funds as a reward if the remaining 90% were returned, thus avoiding legal action. The victim stated:
“We both know there is no way to clean these funds. You will be tracked. We also understand that the phrase ‘good night’s sleep’ does not pertain to your moral and ethical qualities. Yet, we are officially managing your 10% right. Return the 90%.”
On May 9, another account ending in 72F1 responded by sending the victim 51 Ethereum. 72F1 also received money through various intermediary accounts from FakePhishing327990, indicating it was under the attacker’s control.
Intriguing Attack Details
Negotiation, occurred after the attacker allegedly deceived the victim into mistakenly sending 1.155 Wrapped Bitcoin (WBTC) to their account through an address poisoning operation. Blockchain data from May 3 shows the attacker used a smart contract to transfer 0.05 tokens from the victim’s account to the attacker’s account. The transferred token had no name on Etherscan and was referred to only as ERC-20.
Normally, an attacker cannot transfer a token without the user’s permission. However, in this case, the token had a special design that allowed it to be transferred from one account without the user’s consent.
On the same day, the victim apparently mistakenly sent 1.155 WBTC to this address. The address might have appeared similar to one the victim used to deposit money into a central exchange or for another reason. The victim had previously seen that they had sent 0.05 tokens to this address and thus might have assumed it was safe. However, it was revealed that the 0.05 tokens were sent by the attacker and only came from the victim.

 Türkçe
Türkçe Español
Español