Avalanche and Blockaid announced a partnership to integrate Blockaid’s security features directly into Avalanche’s native wallet, Core. The security upgrade aims to prevent increasingly complex phishing scams and hacks plaguing decentralized finance by pre-scanning transactions against Blockaid’s database of known malicious threats and alerting the user before the transaction is signed and broadcast.
Blockaid and Avalanche Partnership
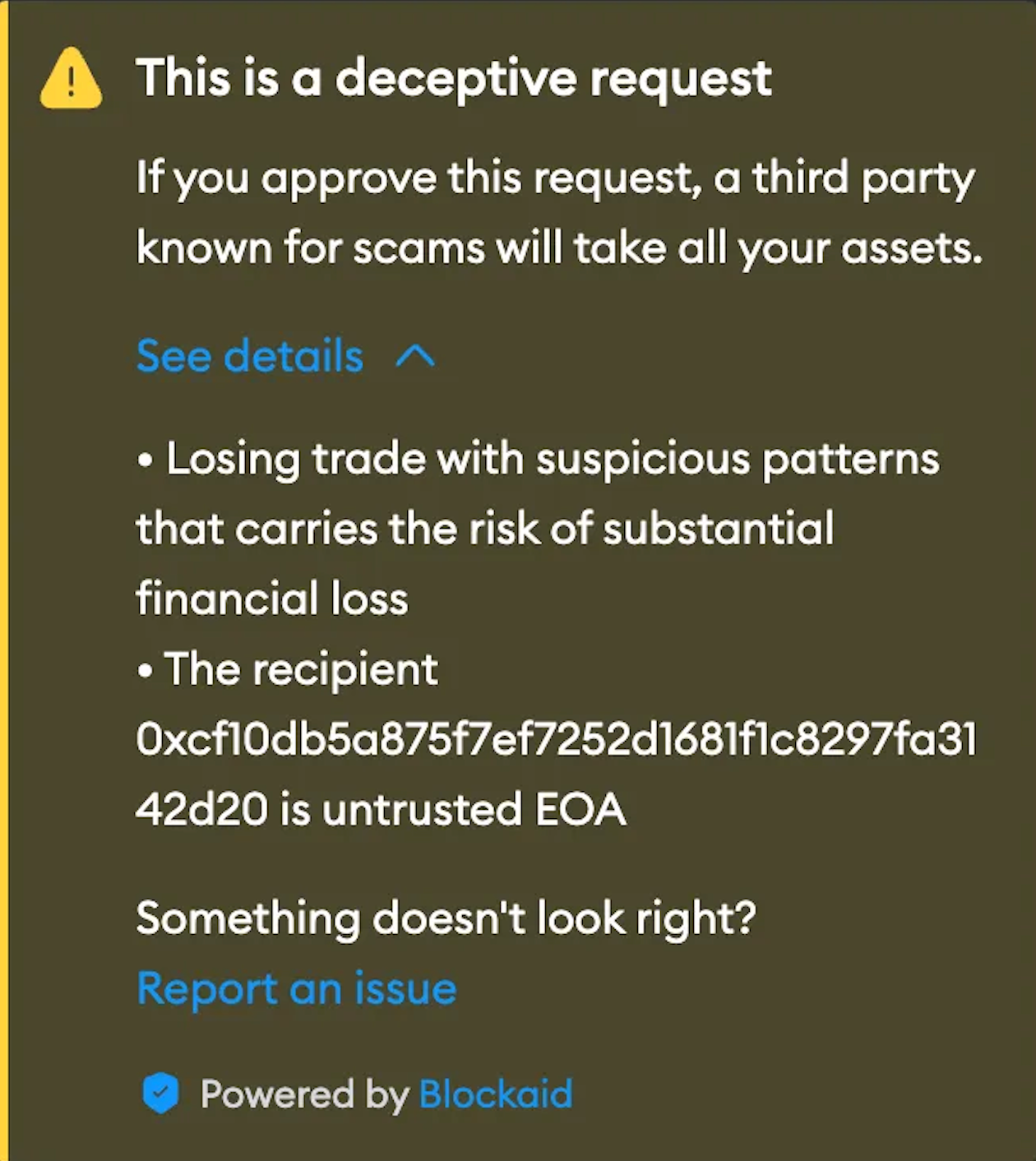
Blockaid claims its security apparatus has helped block 1.3 million attacks and is currently used to protect products offered by OpenSea, MetaMask, Zerion, Coinbase, and Rainbow. Following the collaboration, Ava Labs’ head of consumer products Akash Gupta stated:
“This collaboration with Blockaid represents a significant step forward in providing users with security and control without compromising speed and ease of use. By integrating advanced security solutions into the Core package, we ensure users can explore the Avalanche ecosystem and beyond with peace of mind.” Crypto Traders Are Rushing to This App – Here’s Why You Should Too
However, critics of Blockaid argue that its security scanning features lead to too many false positives, a situation Blockaid considers a feature rather than a flaw of its security software.
Blockchain and Security Process
Security firm officials explained that too many false positives are a better outcome than loosening scanning criteria and allowing malicious actors more gaps to exploit for illegal activities. In the cat-and-mouse game of cybersecurity, there is an evolving threat landscape where transaction simulators must stay one step ahead.
According to cybersecurity expert Bernhard Mueller, malicious software like the notorious Angel Drainer could potentially penetrate the security layers provided by transaction simulators such as Blockaid, WalletGuard, and Pocket Universe. Mueller explained that Angel Drainer might avoid transaction simulators by dynamically creating unsigned contract addresses and attempting to steal funds through these addresses, but these methods are not foolproof or guaranteed to succeed.
The white-hat hacker admitted that his tests using the dynamic, unsigned method caused Blockaid to flag the transaction as suspicious and send a warning alert.


 Türkçe
Türkçe Español
Español