Cryptocurrencies hold varied significance for different individuals. While a few early investors believe it has the potential to change the world, the number of early maximalists of Bitcoin might have decreased, yet some still believe it truly offers an alternative to the current system. A significant group is involved in crypto merely to make money. But what about the others?
Lazarus and Cryptocurrencies
There are individuals working to identify the perpetrators behind cyber attacks on cryptocurrencies. Among the most famous is ZachXBT, who even receives support from government agencies when needed. We recently discussed the harassing extent of emails from a U.S. IRS agent. ZachXBT is one of the most renowned experts in this field.
ZachXBT recently discussed some figures related to the activities of the North Korean hacker group Lazarus. This group works directly for the North Korean government, and a significant portion of their loot goes to the state for armament activities.
How Much Did They Launder?
According to research by crypto detective ZachXBT, North Korea’s Lazarus Group laundered a total of $200 million worth of cryptocurrency between August 2020 and October 2023. The primary reason for the U.S. war against cryptocurrency mixers was also shown as Lazarus and other hacking groups heavily using them.
“Thousands of people have been directly and indirectly affected by Lazarus Group attacks, and this number seems likely to continue increasing.”
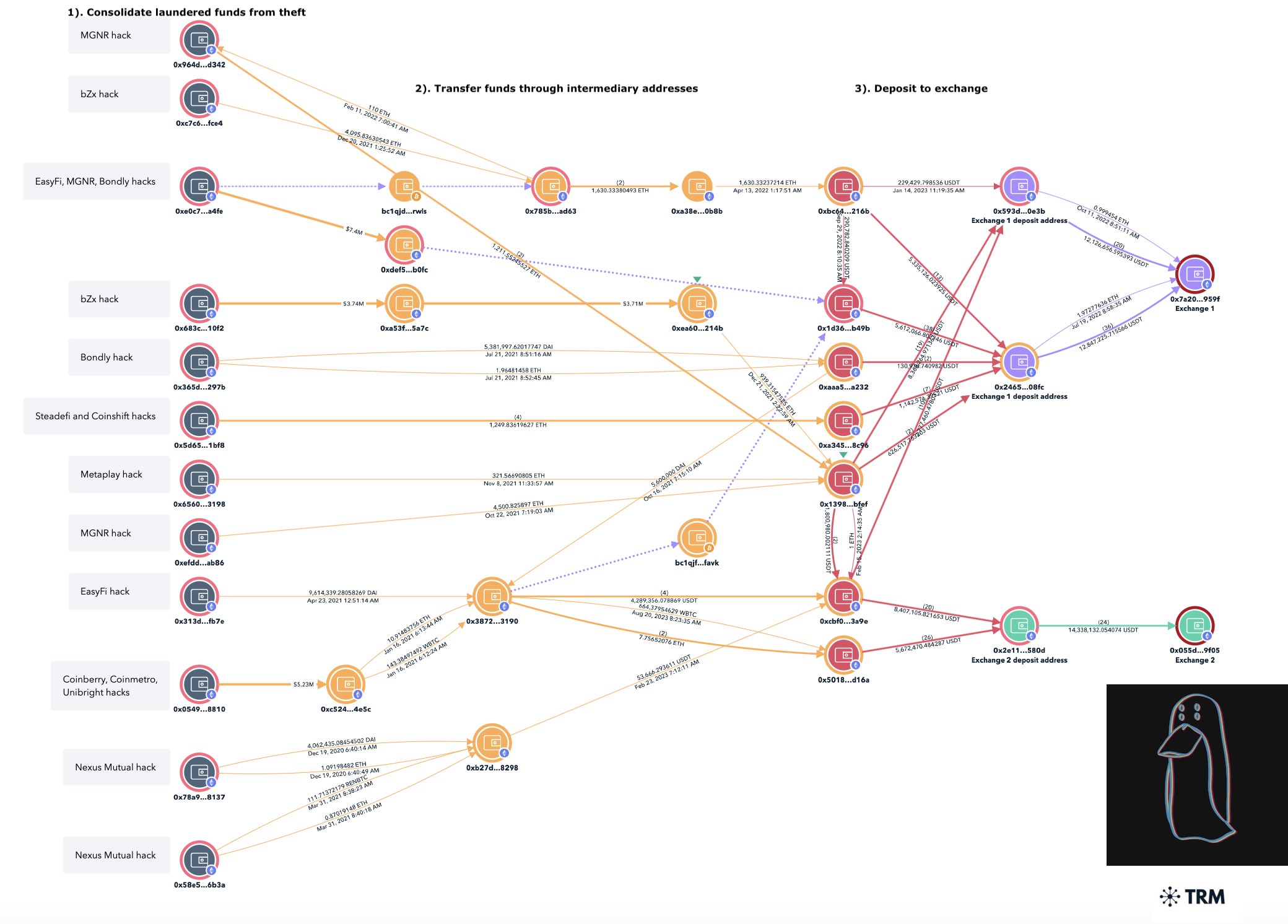
Attackers use a variety of methods from technical vulnerabilities to social engineering attacks, signing off on major incidents like the $100 million Harmony bridge exploit in January 2023 and the Ronin bridge hack in March 2022. During the Ronin bridge hack, they approached team officials with attractive job offers to obtain the keys.
Ronin incident’s method is also commonly used in hacking major YouTube accounts like Ruhi Çenet. One day, you receive convincing messages via Telegram or email, and you discuss the offered deal for a long time. Then, you receive a PDF for an advertisement proposal and job application to review. Opening this file results in your passwords, files, and complete control of your device falling into the attackers’ hands.

 Türkçe
Türkçe Español
Español