A developer from Munchables managed to convince the Munchables hacker to change their mind and return the stolen open-source $62.8 million worth of Ethereum without demanding a ransom, a process that took about eight hours. On March 26th, around 12:30 PM, the Ethereum-based NFT game project Munchables reported an attack that drained over 17,400 Ethereum from the GameFi application.
The Hack Attack Shook the Industry
Munchables, along with blockchain researchers like PeckShield and ZachXBT, began tracking the movements to stop the stolen funds. ZachXBT claimed that the attack stemmed from the Munchables team hiring a North Korean developer known by the alias Werewolves0943.
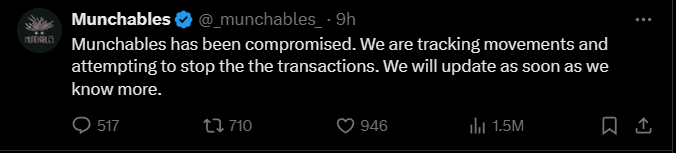
At 07:40 AM on March 27th, Munchables identified that the computer hacker was one of their own developers. After an hour of negotiations, the former developer agreed to return the hacked funds. Munchables made an official statement saying:
“The Munchables developer shared all the private keys necessary to help recover the user funds. This included the key holding $62,535,441.24, the key holding 73 WETH, and the owner key containing the rest of the funds.”
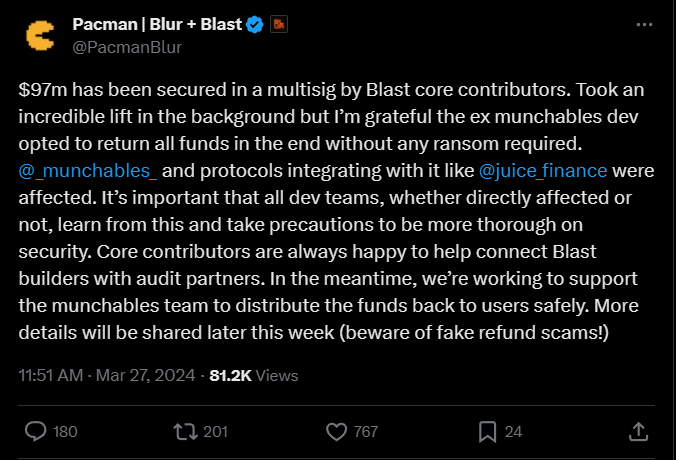
The creator of Ethereum Layer-2 blockchain network Blast, known by the alias Pacman, thanked ZachXBT for his support and announced that the former Munchables developer eventually chose to return all the funds without any ransom.
Blockchain Space and Hack Attacks
Since Munchables is built on the Blast blockchain network, Pacman will work with the Munchables team to help redistribute the stolen and now recovered funds. In the meantime, victims of the hack are advised to follow communications only from official sources to avoid repayment scams.
The aforementioned attack occurred about four days after a hacker stole approximately $24,000 from the decentralized finance (DeFi) aggregator ParaSwap’s address. The protocol managed to recover the funds and began reimbursing users.
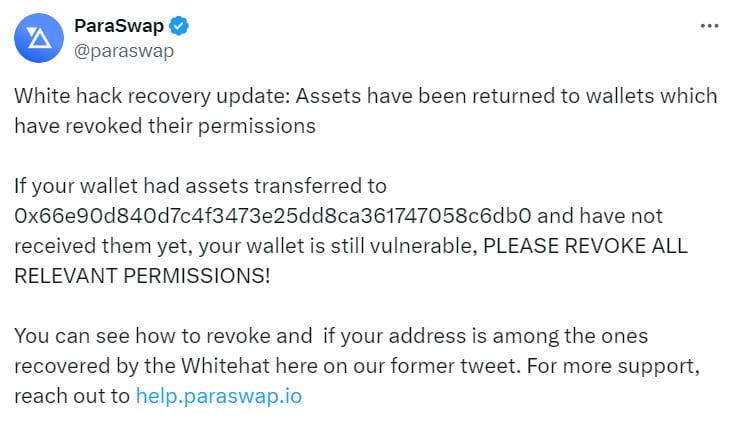
ParaSwap successfully resolved the issue with the help of white-hat hackers and revoked permissions for the vulnerable AugustusV6 smart contract. ParaSwap revealed that a total of 386 addresses were affected by the vulnerability. However, as of March 25th, permissions related to the faulty contract had not yet been revoked for 213 addresses.

 Türkçe
Türkçe Español
Español