One of the leading decentralized finance (DeFi) protocols, ALEX Lab, fell victim to a significant security breach. In the attack targeting the protocol, hundreds of thousands of dollars worth of various cryptocurrencies were stolen.
$4.3 Million Funds Withdrawn from Protocol
The attack was carried out by targeting ALEX’s XLink bridge, a service that allows token transfers between different Blockchain networks. Security researcher CertiK indicated that the hacker likely gained control of the private key associated with the bridge. As a result, the hacker managed to withdraw and transfer a total of $4.3 million worth of Bitcoin, stablecoins, and Sugar Kingdom tokens from the protocol.
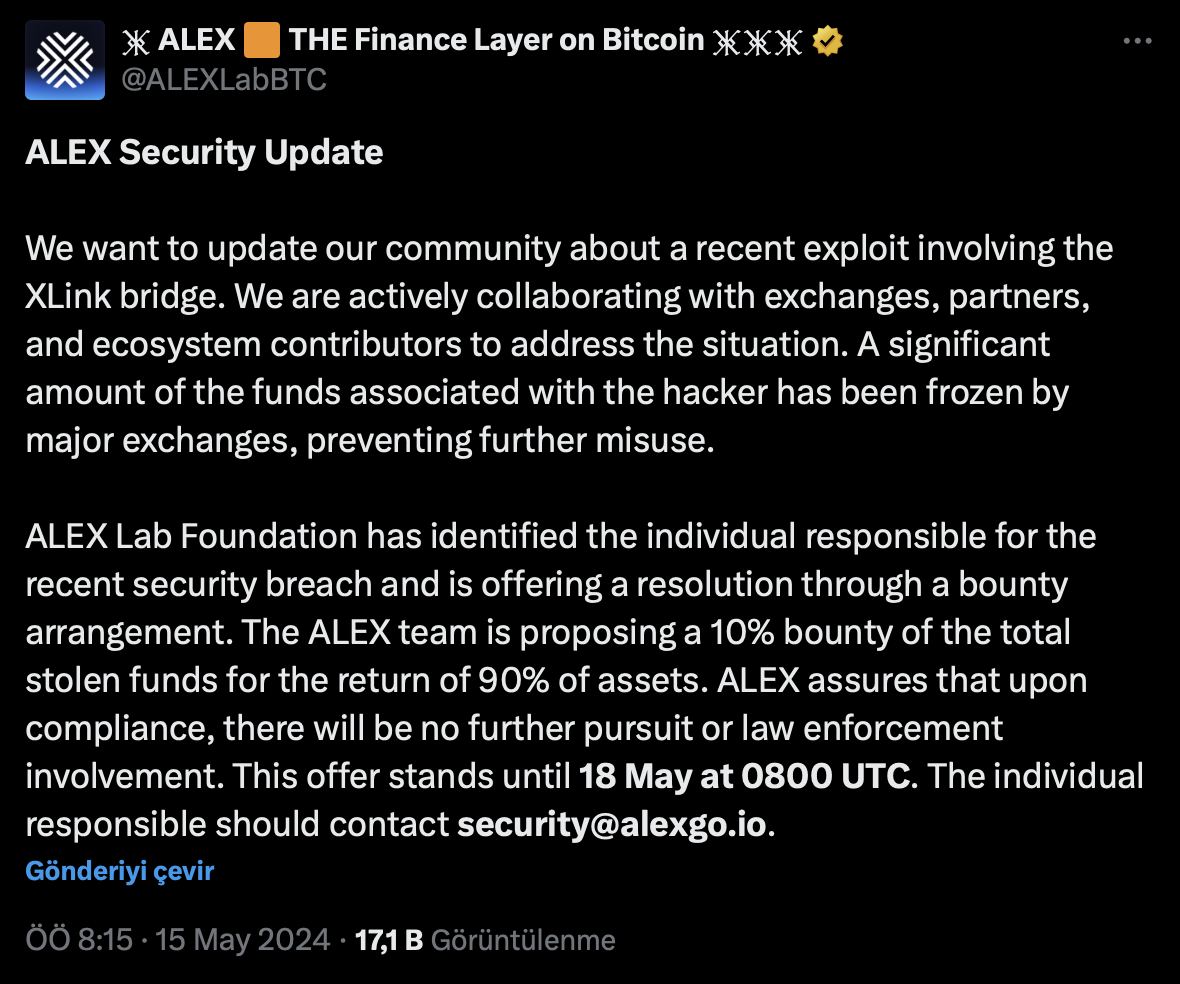
ALEX Lab developers quickly confirmed the hack attack and claimed to have identified the hacker. In response, they offered a 10% reward for the return of 90% of the stolen funds. The developers aim to recover the stolen funds from the protocol through this method. They guaranteed no follow-up or law enforcement intervention if the terms were met and presented the offer with a specific deadline.
Crypto Exchanges Act, Funds Frozen
Following the hack attack, major crypto exchanges froze the funds associated with the hacker to prevent misuse. The swift action of crypto exchanges after the incident reflects the ongoing effort to mitigate the impact of hack attacks in the crypto world and protect users’ funds. By freezing the stolen funds, crypto exchanges aim to safeguard their platforms and prevent illegal activities.
Private key based hack attacks are a common method used by hackers in the crypto world. As seen in various major hack attacks in the past, security vulnerabilities can lead to significant losses, highlighting the importance of private key security. Examples of hack attacks using private keys in the crypto world include the theft of $650 million from Ronin and $100 million from Harmony.
The hack attack on ALEX Lab once again emphasized the importance of taking robust security measures in the DeFi ecosystem. As the sector continues to grow rapidly, ensuring the security of protocols and platforms remains crucial to maintaining user trust. Therefore, developers and stakeholders must take solid security measures to reduce the risk of future hack attacks.

 Türkçe
Türkçe Español
Español








